Standards risk-based Methodology, Transparent Grading
Know exactly where your data comes from.
THE ARCHITECTURE
Non-intrusive & Passive Scan
Designed for Accuracy
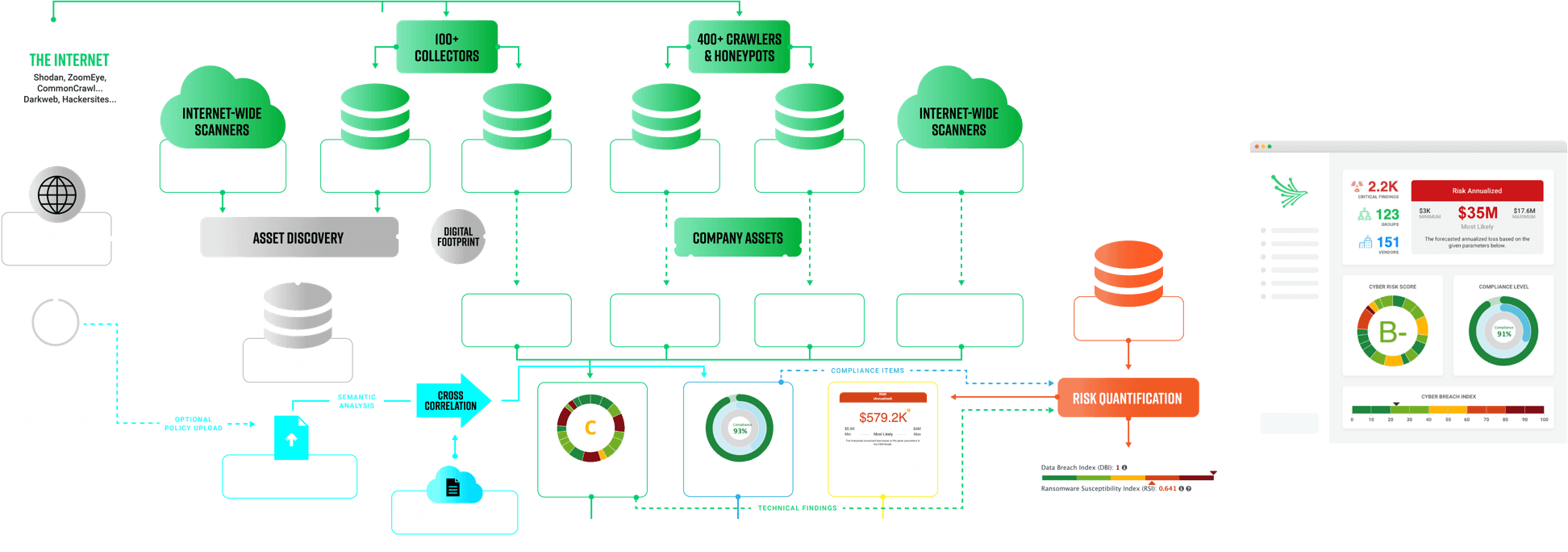
Non-intrusive scans using open-source intelligence (OSINT) techniques collect data from 400+ OSINT resources from a span of internet-wide scanners, without ever touching the target.
As an authorized IP zone transferer with one of the largest IP & Domain Whois databases, we hold more than one billion (1B) historical items. The asset-discovery engine identifies every company-related IP address and domain names.
Standard scoring models eliminates false positives, such as the MITRE Cyber Threat Susceptibility Assessment (CTSA), Common Weakness Risk Analysis Framework (CWRAF), Common Weakness Scoring System (CWSS), Common Vulnerability Scoring System (CVSS), and Factor Analysis of Information Risk (FAIR).
Data is analyzed and compiled into a simple, readable report with letter-grade ratings to identify and mitigate potential security risks as well as convert technical data into business concepts.
Asset Discovery
Establish Assessment Scope
The first step in CTSA is to establish the scope of the evaluation, which can be characterized in terms of:
- The set of system assets being evaluated
- The range of attack TTPs being considered
- The types of adversaries
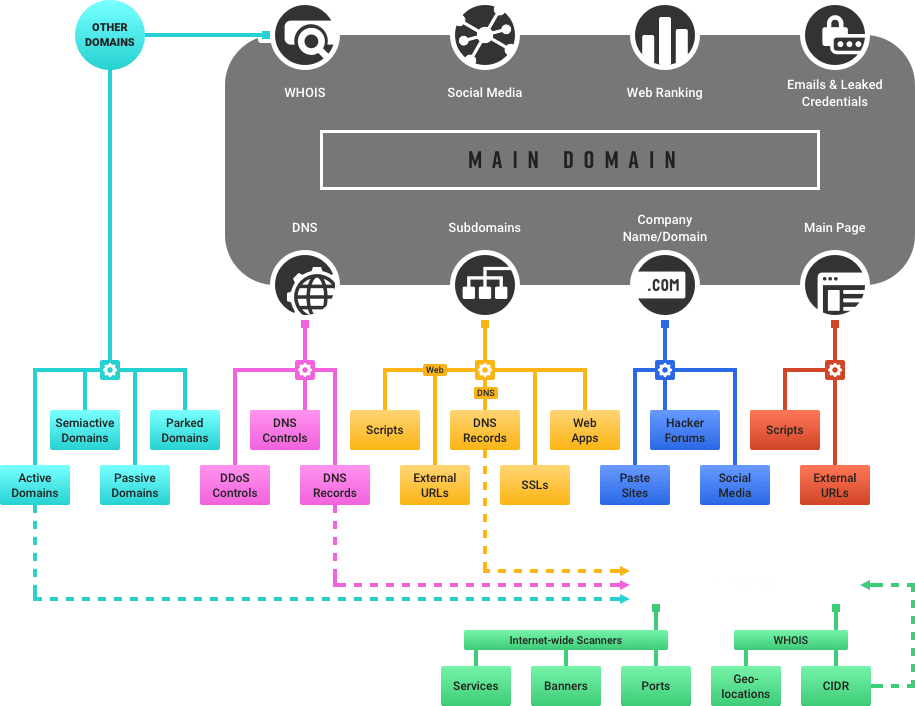
Black Kite establishes the assessment scope during the asset discovery process, which discovers all publicly visible accessible domains, subdomains, IP/CIDR ranges, etc.
Identify Candidate TTP
Once the scope of CTSA is established, the next step is to evaluate the cyber asset’s architecture, technology, and security capabilities against TTPs in the Mission Assurance Engineering (MAE) Catalog. Unclassified sources of adversary TTPs in the catalog include MITRE-hosted resources such as Common Attack Pattern Enumeration and Classification (CAPEC), Common Weakness Enumeration (CWE), and Common Vulnerability Enumeration (CVE). CAPEC is a compilation of attack patterns derived from specific real-world incidents. CWE is a catalog of software weaknesses and defects that adversarial TTPs may exploit. CVE catalogs vulnerabilities found in Commercial off-the-shelf (COTS) hardware and software products.
Eliminate Implausible TTPs
This initial set of candidate TTPs undergoes a narrowing process to eliminate TTPs considered implausible. Several factors can make a TTP an implausible method of a cyber attack. Many TTPs have prerequisites or conditions that must hold true in order for that TTP to be effective.
Apply Scoring Model
Candidate TTPs that cannot be eliminated are ranked using a scoring model. The TTP scoring model assesses the risk associated with each TTP relative to the other 10 plausible TTPs considered in the assessment. This ranking helps set priorities on where to apply security measures to reduce the system’s susceptibility to cyber-attack. CAPEC severity levels, CVSS scores, and CWE severity ranks are the main parameters to calculate the TTP risk scores.
Construct a Threat Matrix
CTSA produces a Threat Matrix, which lists plausible attack TTPs ranked by decreasing risk score and their mapping to cyber assets as a function of adversary type. Black Kite has over 500 TTPs (APPSEC001, APPSEC002, … DNS001, DNS002,… etc.) with different risk scores.
The Black Kite threat matrix is calculated by using the Common Weakness Scoring System (CWSS™) that provides a mechanism for prioritizing software weaknesses in a consistent, flexible, open manner. It is a collaborative, community-based effort that is addressing the needs of its stakeholders across government, academia, and industry. When used in conjunction with the Cyber Threat Susceptibility Assessment (CTSA) or Common Weakness Risk Analysis Framework (CWRAF™), organizations are able to apply CWSS to those CWEs that are most relevant to their own specific businesses, missions, and deployed technologies.
Our Risk Management Methodology Grading Scale
| Letter Grade | Percentage |
|---|---|
| A+ | 97%+ |
| A | 93%-96% |
| A- | 90%-92% |
| B+ | 87%-89% |
| B | 83%-86% |
| B- | 80%-82% |
| C+ | 77%-79% |
| C | 73%-76% |
| C- | 70%-72% |
| D+ | 67%-69% |
Category Weights
The category grades are calculated once assessments on all the categories are completed. Each category has a different weight in the overall grade as shown below.
| Category Name | Weight (Total 100) | Category Name | Weight (Total 100) |
|---|---|---|---|
| Digital Footprint | 0/100 | IP Reputation | 7/100 |
| Email Security | 6/100 | Social Network | 3/100 |
| SSL/TLS Strength | 6/100 | Attack Surface | 4/100 |
| Application Security | 9/100 | Brand Monitoring | 3/100 |
| Fraudulent Apps | 3/100 | Website Security | 6/100 |
| DNS Health | 6/100 | Hacktivist Shares | 5/100 |
| DDoS Resiliency | 4/100 | Patch Management | 10/100 |
| Network Security | 6/100 | Web Ranking | 2/100 |
| Fraudulent Domains | 5/100 | Information Disclosure | 3/100 |
| Credential Management | 9/100 | CDN Security | 3/100 |
Trusted By



Black Kite vs. Competitors
Key players in the Security Rating Services (SRS) market (Black Kite, BitSight, SecurityScorecard, RiskRecon, and UpGuard) focus on publicly accessible, external data sources when performing vendor assessments. Although each player has a different approach, all providers in the SRS market use similar resources and techniques to collect data.
However, not all SRS providers are equal in terms of usability, analytics, compliance, technical depth, and threat intelligence capabilities. Compare Black Kite’s Cyber Risk Rating with other SRS products in the market to help you make a better-informed decision.
Legend
-
Limited and Accurate
-
Limited
-
Partial
-
Complete/Available
-
Extensive
-
Not Available

Usability
Speed
Methodology
Compliance
Technical Depth
Threat Intelligence
ANALYTICS
Other
FREQUENTLY ASKED QUESTIONS
What is our Methodology?
What is third-party risk management?
How does Black Kite score vendors?
Why is continuous monitoring important?
Why Black Kite?
What is a passive scan?
Do I need permission to scan a vendor?
What Is the cost?
Looks great, how do I test drive?
What is OSINT?
What is OPEN FAIR?
What regulations and frameworks are covered in the Compliance module?
How do you validate findings?
What information do you provide to improve my vendor’s score?
How often does Black Kite update its grading methodology?


