The Gray Rhino
Makhosi is a newborn female white rhino calf rescued when rangers noticed she was unable to suckle from her mother, and without human intervention, she would not survive if left in the wild.
We want to eradicate the gray rhino in the cyber risk world; however, we strongly support saving them in the real world.
Black Kite Team

What is a Gray Rhino?
In the book Gray Rhino, author Michele Wucker says, “A ‘gray rhino’ is a highly probable, high impact yet neglected threat: kin to both the elephant in the room and the improbable and unforeseeable black swan.”
Black Kite believes the risk companies face today from the supply chain is truly a gray rhino. Our philosophy is to help our clients identify their ‘third-party gray rhinos’ before they become an issue. In the animal kingdom, Rhinos are an endangered species. While we want to eradicate the gray rhino in the risk world, we strongly support saving them in the real world. To that effect, Black Kite has adopted Makhosi, an orphaned rhino through Helping Rhinos.
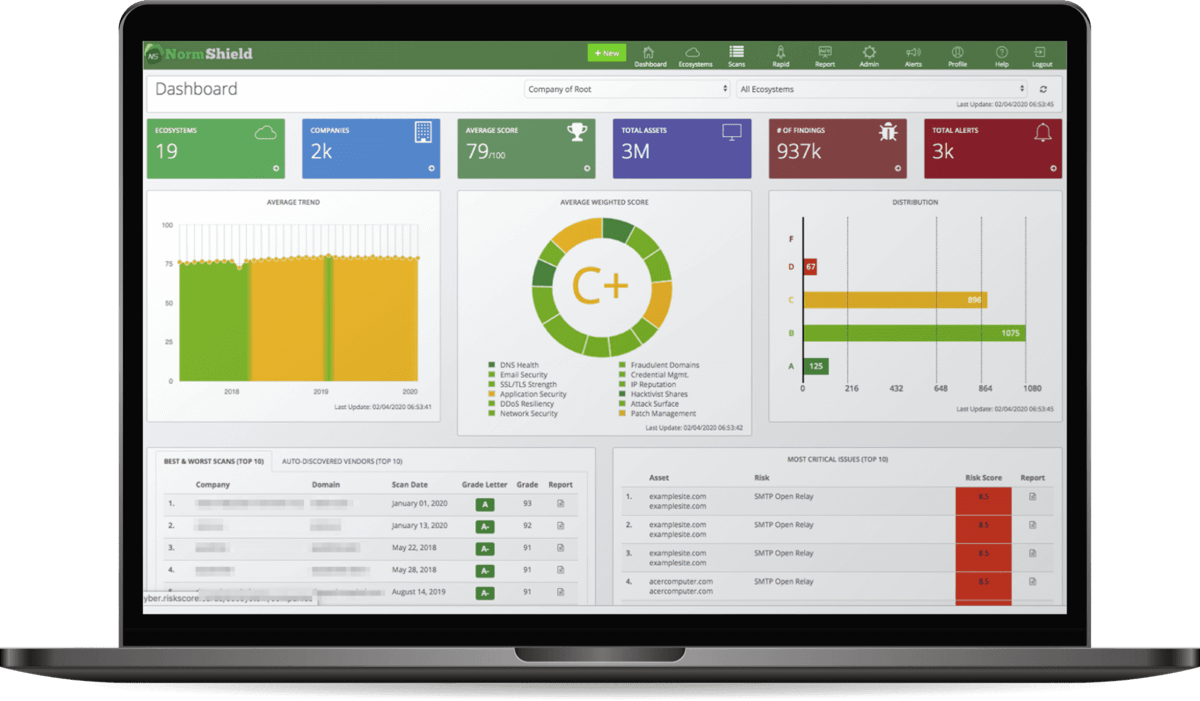
Discover Your Gray Rhinos
Black Kite is the only cyber rating system that accurately monitors your ecosystem and provides improved management of your assets. By eliminating false positives and providing tools to fix risk levels across their externally facing digital footprint, our platform makes organizations more resilient. Eliminate gray rhinos in your ecosystem today with a free cyber rating.
Free Cyber Rating
The Zulu Royal family witnessed the team busy setting up drips to stabilize her condition in the back of their vet vehicle, in a garage en route to the Orphanage. They named and blessed Makhosi, meaning leader or royalty in the Zulu language.
trusted by